NTP Amplification Attacks Explained: Your Ultimate Guide to Understanding and Prevention
What is an NTP Amplification Attack?
The Network Time Protocol (NTP) is crucial for synchronizing clocks on internet-connected computers. It operates via UDP port 123, receiving time data from internal or external sources. Older NTP versions include a monitoring feature, allowing administrators to query traffic counts on the NTP server using a command called “monlist”. This command sends a list of the last 600 connected machines to the requesting device.
Understanding NTP Amplification Attacks
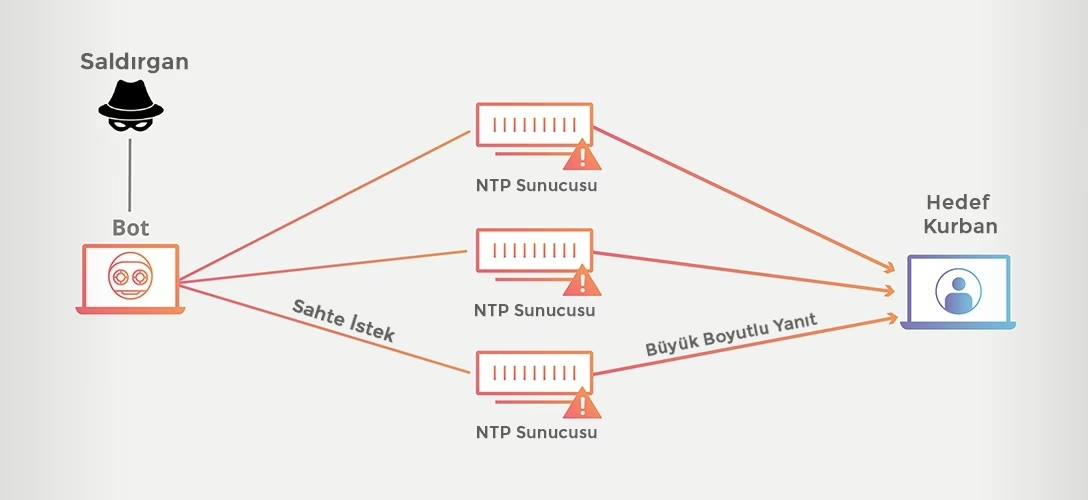
An NTP Amplification attack is a form of Distributed Denial of Service (DDoS) attack. Attackers exploit public NTP servers to inundate a target system’s network with excessive packets, causing traffic slowdowns or complete system unavailability. This is a type of reflection attack, where servers are deceived into sending responses to a spoofed IP address—the target’s IP.
NTP Amplification vs. DNS Amplification Attacks
Similar to NTP Amplification, DNS Amplification Attacks involve sending fake DNS requests to DNS servers. In a typical DNS Amplification attack, the request-to-response ratio is 1:70, meaning 1 Gbps of requests can generate 70 Gbps of traffic. NTP Amplification attacks can have even higher ratios, ranging from 1:20 to 1:200 or more.
How NTP Amplification Attacks Work
Attackers use tools like Metasploit Framework or Open NTP Project to send fake requests to public NTP servers, overwhelming the target system’s network bandwidth. These attacks are usually executed using multiple botnets, requiring only the target system’s IP address.
The Role of Botnets
Botnets are used to send small, malicious requests to public NTP servers. The source IP address in these requests is spoofed to match the target system’s IP. The malicious requests (e.g., MON_GETLIST) cause the NTP servers to send responses to the target system. Each response contains data about the last 600 machines connected to the server.
Amplification Factor
The requests sent to NTP servers trigger an amplification factor, resulting in large responses that flood the target system. This causes network congestion, traffic slowdowns, and system unavailability. Attackers use botnets and UDP to remain anonymous, as UDP does not require a three-way handshake like TCP, allowing for quick and insecure packet transmission.
Steps of an NTP Amplification Attack
- Botnet Utilization: The attacker uses a botnet to increase the attack’s magnitude and hide their identity.
- Sending UDP Packets: The botnet sends UDP packets with a spoofed IP address to public NTP servers with the monlist command active.
- Request and Response: Each UDP packet uses the monlist command to request and receive a large response.
- Forwarding Responses: The NTP server sends the responses to the target system, specified as the spoofed IP address.
- Network Congestion: The target system receives the responses, causing network bandwidth to fill up, traffic to slow down, and service interruptions to occur.
NTP Amplification Attack Scenario
DDoS attacks aim to take target systems offline. NTP Amplification attacks are among the most effective DDoS techniques. To execute an NTP Amplification attack, the following are required:
- An automated tool to send requests to NTP servers
- Botnets to hide the attacker’s identity and increase the attack’s intensity
- A list of vulnerable NTP server IPs
NTPDoser Tool
One such tool is NTPDoser, which can be used to carry out NTP Amplification attacks. The tool can be downloaded from GitHub or cloned in a Linux environment using the command git clone https://github.com/DrizzleRisk/NTPDoser.git.
Compiling and Using NTPDoser
After downloading, the C++ source code can be compiled using the command gcc NTPDoser.cpp -o NTPDoser -lstdc++ -pthread. The compiled NTPDoser file can then be used to execute an NTP Amplification attack with the command ./NTPDoser [target_IP] [thread_count] [attack_duration].