Understanding the Shared Responsibility Model in Cloud Security
Understanding the Shared Responsibility Model in Cloud Security Cloud environments have become the backbone of most IT and application…
Cyber Security

Understanding the Shared Responsibility Model in Cloud Security Cloud environments have become the backbone of most IT and application…
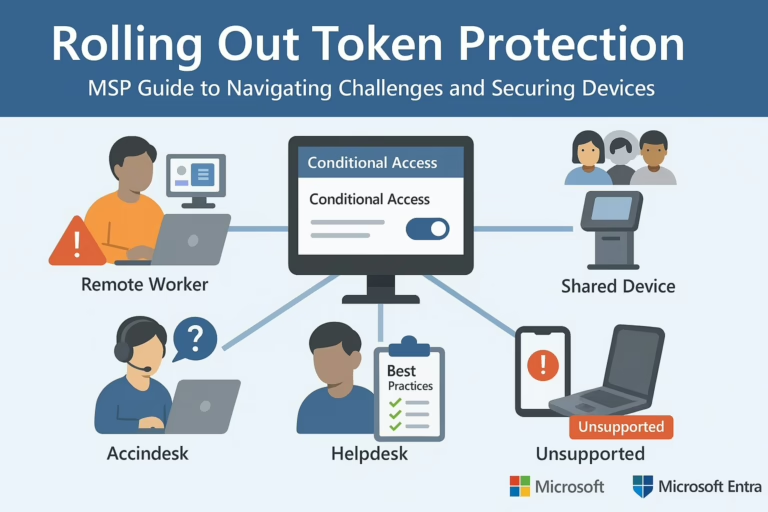
Microsoft Token Protection Rollout: Essential Guide for MSPs In the first part of our Microsoft Entra Security Series, we…

Understanding Social Engineering Social engineering is one of the oldest and most effective forms of cyber attacks in the…

What is Penetration Testing? Penetration Testing, often referred to as Pentest, is a security testing process used to identify…
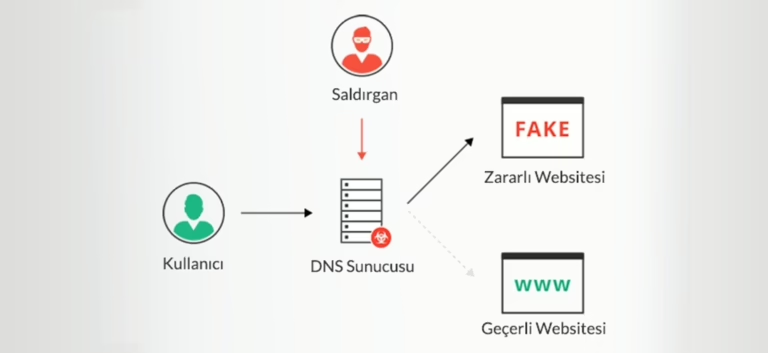
Understanding DNS Hijacking To comprehend DNS Hijacking, it’s essential to grasp the concept of DNS and its functionality. DNS,…
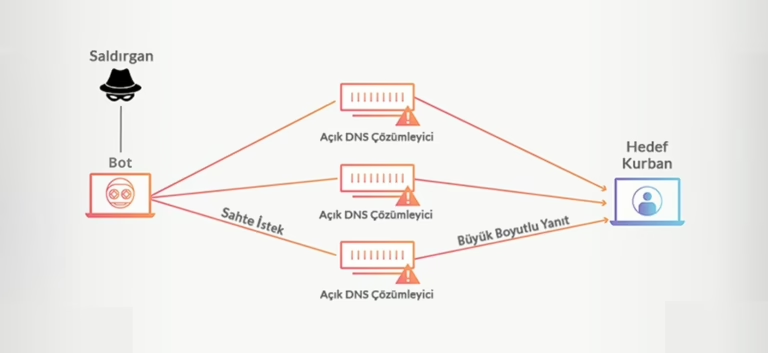
What is a DNS Amplification Attack? A DNS Amplification Attack is a type of Distributed Denial-of-Service (DDoS) attack. Like…

Understanding Network Security and Data Packets Networks, whether small or large, are an integral part of our daily lives….

Aura vs LifeLock: Which identity theft protection is truly better? We compare features, 3-bureau credit monitoring, VPN, antivirus, family plans, and pricing for 2025. Find out who actually protects you.
Facing a slow, crashing, or ad-ridden PC? You likely need a definitive guide on How to Remove Malware. Malware…

In the rapidly evolving threat landscape of 2026, the Cybersecurity Budget is no longer a necessary expense; it is…
End of content
End of content