Understanding OSI and TCP/IP Models: Key Differences and Importance in Cybersecurity
Understanding OSI and TCP/IP Models
The OSI model defines how devices communicate over networks. Developed by the International Organization for Standardization (ISO), the Open Systems Interconnection (OSI) model is a set of communication protocols. This model quickly gained acceptance and became widespread during the early days of the internet, serving as a guide for network operations. Initially, each brand had its own communication model for its devices. However, as networks grew and expanded, this situation became problematic, leading to the development of the OSI model as a manufacturer-independent communication standard. Consequently, all manufacturers began to implement communication methods according to this model. The TCP/IP model emerged as a simpler and more communication-friendly alternative to the ISO model.
In the world of cybersecurity, it is essential to be familiar with the OSI and TCP/IP models. Understanding the layers within these models and their functionalities is crucial for gaining experience in network management, which is a vital step in entering the field of cybersecurity.
The Necessity of OSI Model
Before the OSI model, most commercial networks used by small or large companies were built with technologies that could not be standardized by a specific enterprise. With the spread of communication, OSI emerged as an industry necessity in the late 1970s to create a network that could connect products from various manufacturers. The OSI model, known in Turkish as “Açık Sistemler Bağlantısı,” explains how networks communicate. It describes the relationships between various protocols and activities by explaining different protocols and functions.
The OSI model is classified into seven layers. It was introduced by the International Organization for Standardization (ISO) in the 1980s and began to spread rapidly.
Network: The Foundation of Cybersecurity
We often hear the phrases “The foundation of cybersecurity is the network” and “You can’t have cybersecurity without understanding networks.” I wholeheartedly agree with these statements. The network is essentially the foundation of a building. Without this foundation, any knowledge you add will eventually collapse. To understand networks, it is essential to understand the TCP/IP and OSI models.
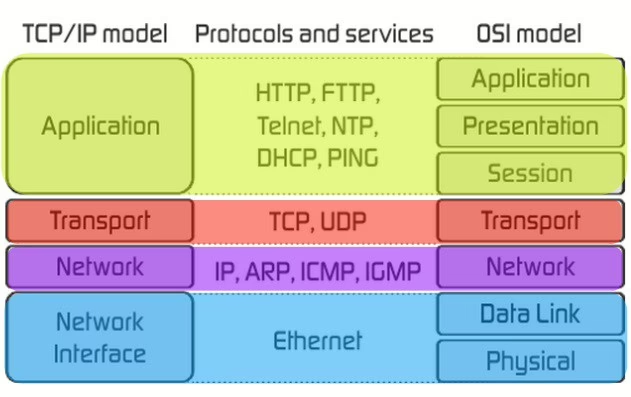
What are the TCP/IP and OSI Models? What are their Differences?
Let’s examine them briefly and concisely.
OSI and TCP/IP Models
It is generally known that the structure forming the basis of internet and network infrastructure is the OSI model. However, the structure we use in today’s internet world is actually the TCP/IP model. The TCP/IP structure has been preferred due to its ease of use. The OSI model, on the other hand, is a more complex model compared to TCP/IP.
OSI and TCP/IP Models and Their Differences
| Layers | Description | Protocols |
|---|---|---|
| Application (7) | This layer directly interfaces with applications and performs common application services for application processes. | POP, SMTP, DNS, FTP, Telnet, HTTPS |
| Presentation (6) | These are applications related to syntactic differences in data presentation in end-user systems. | Network Data Representation (NDR), Lightweight Presentation Protocol (LPP) |
| Session (5) | It provides a mechanism for managing the dialogue between end-user application processes. | NetBIOS |
| Transport (4) | It provides end-to-end communication control. | TCP, UDP |
| Network (3) | It routes information on the network. | IP, ARP, ICMP |
| Data Link (2) | It describes the logical organization of data bits transmitted in a specific medium. | SLIP, PPP |
| Physical (1) | It describes the electrical properties of the exchanged signals and their interpretation, as well as the physical characteristics of various communication media. | IEEE 1394, DSL, ISDN |
Layers of the OSI Model
The OSI model does not change according to any hardware or computer network type. The standard is unique and applied without change. As the ISO standard is divided into seven layers, these seven layers are specified as follows. For data transmission both within and outside the network, the data must pass through each layer according to the determined rules. At each layer, certain tasks are assigned to the data.
When data is sent, it receives a separate header at each layer. When the data reaches the opposite computer, it goes according to these headers from the hardware layer (physical layer) to the application layer. When it finally reaches the application layer, the data will have reached the opposite computer.
Physical Layer
This is the layer where the data link is transmitted as electrical signals. The answer to the question of how we are connected to the network is determined in this layer. The physical layer is the actual NIC and Ethernet cable. It defines the relationship between a device and its transmission medium (such as fiber, copper, radio signal). It also explains these transmission modes such as simplex, half duplex, and full. The resolution of bits takes place on this layer. The resolved bits are sent as digital or analog signals. Generally, raw data is processed in this layer. No information such as the type of data or its destination is considered.
Data Link Layer
It is defined as the data link layer where data transfer between endpoints is provided. It is known as the layer where our wired or wireless Ethernet card takes the MAC address and the ARP protocol works. It detects errors that may occur in the physical layer and is the layer where these errors are corrected as much as possible. On this layer, the protocol that enables establishing a connection between two physically connected devices and terminating this connection is defined.
Network Layer
The network layer ensures the transfer of a data packet from one network node to another network node. At this layer, data begins to be carried as packets. Thanks to this layer, the data is routed via the router. Switching and routing devices operate at this layer. The network layer includes situations where information that routers will use is added to the data packet when it needs to be sent to a different network. The network layer is the layer where the IP address is defined for devices. It is also the layer where the IP address of the opposite system is determined.
At this layer, the best path selection is also made for a data to reach its destination. Usually, the shortest path is preferred. This process is called Routing, and the device that performs this process is called a Router. In the simplest definition, the router aims to ensure that the packet reaches the opposite system in the shortest time by making the best path selection. The protocols used at this layer can be listed as IP, ARP, RARP, BOOTP, ICMP. This layer converts the logical network address into the physical machine address. If the size of the data transmitted from a node operating in the network layer to another node operating in the data link layer is too large, the network divides the data into several pieces, sends the pieces separately, and reassembles these pieces at the node it sends. The network layer does not guarantee that data transmission will be carried out securely.
Transport Layer
It is defined as the transport or transmission layer. The transport layer packetizes the data it receives from the application layer. Packetizing is the whole process of dividing large data into smaller data. The transport or transmission layer is responsible for the security of dividing packets into parts and reassembling them and error control. If the packet encounters an error, it is sent again. It is the layer where it is checked whether the packet has reached the other side and port separation is done, and it is known as the layer where it is determined which port listens to which application.
The transport layer divides the data coming from the upper layers into parts in the size of the network packet. TCP, UDP, SPX protocols operate at this layer. These protocols also perform some tasks such as error control. At this layer, data is carried in segment form.
Examples of protocols in the transport layer are TCP and UDP. Due to the connection-oriented nature of the protocol, the transport layer uses buffering, congestion avoidance, and windowing methods to prevent the loss of packets that have been divided into parts and sent.
Session Layer
The session layer controls the connections between devices. It can establish, manage, or terminate local and remote connections. The session layer mostly uses remote procedure calls in application environments.