Public Wi-Fi Security Measures – What You Need to Know in 2026
Public Wi-Fi Security Measures: What You Need to Know in 2025 Access to the internet has become an indispensable part of our lives today. In cafes, airports, hotels, and…
Network Security
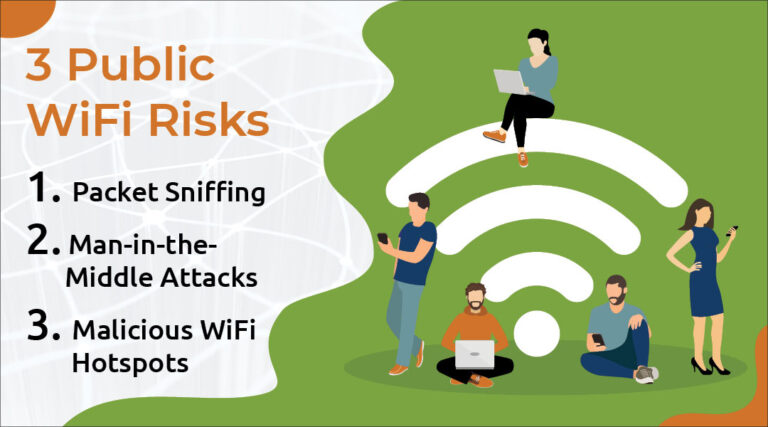
Public Wi-Fi Security Measures: What You Need to Know in 2025 Access to the internet has become an indispensable part of our lives today. In cafes, airports, hotels, and…

In the dynamic cyber landscape of today, effective security requires a comprehensive, multi-layered strategy. Simply relying on a single firewall or antivirus solution is insufficient for Protecting Your Digital Fortress. Instead, security leaders must adopt an architectural approach—a model that views the organization’s assets as a Digital Fortress requiring defense at every conceivable entry point. This 7-Layer Model for Protecting Your Digital Fortress provides a structured framework for CISOs and security professionals to audit, build, and optimize their defense posture, ensuring robust security from the perimeter to the core.
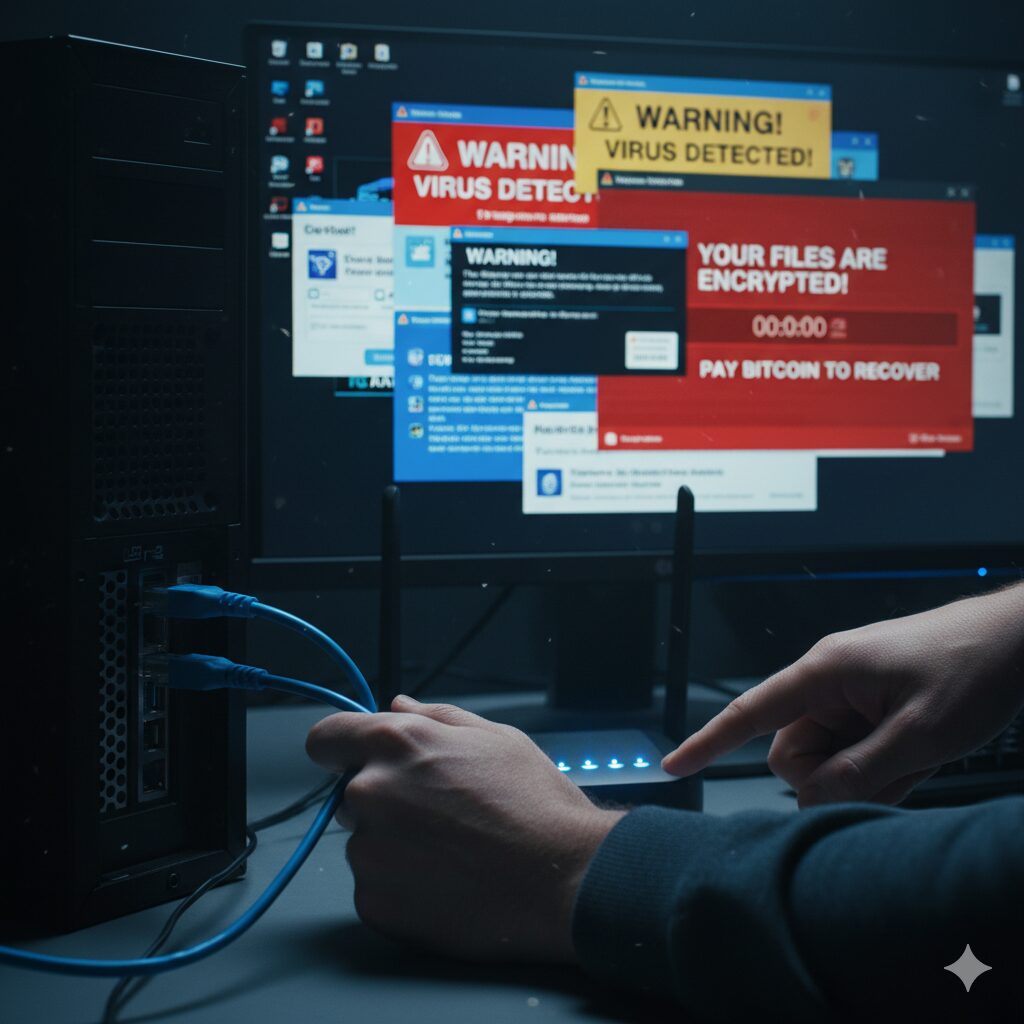
Facing a slow, crashing, or ad-ridden PC? You likely need a definitive guide on How to Remove Malware. Malware (Malicious Software) is an umbrella term covering viruses, spyware, ransomware, and trojans, all designed to compromise your data and privacy. Learning How to Remove Malware effectively is a critical skill for maintaining a healthy and secure digital life. This detailed guide walks you through the step-by-step process of identifying, isolating, and completely eradicating malicious threats, ensuring you know exactly How to Remove Malware safely.
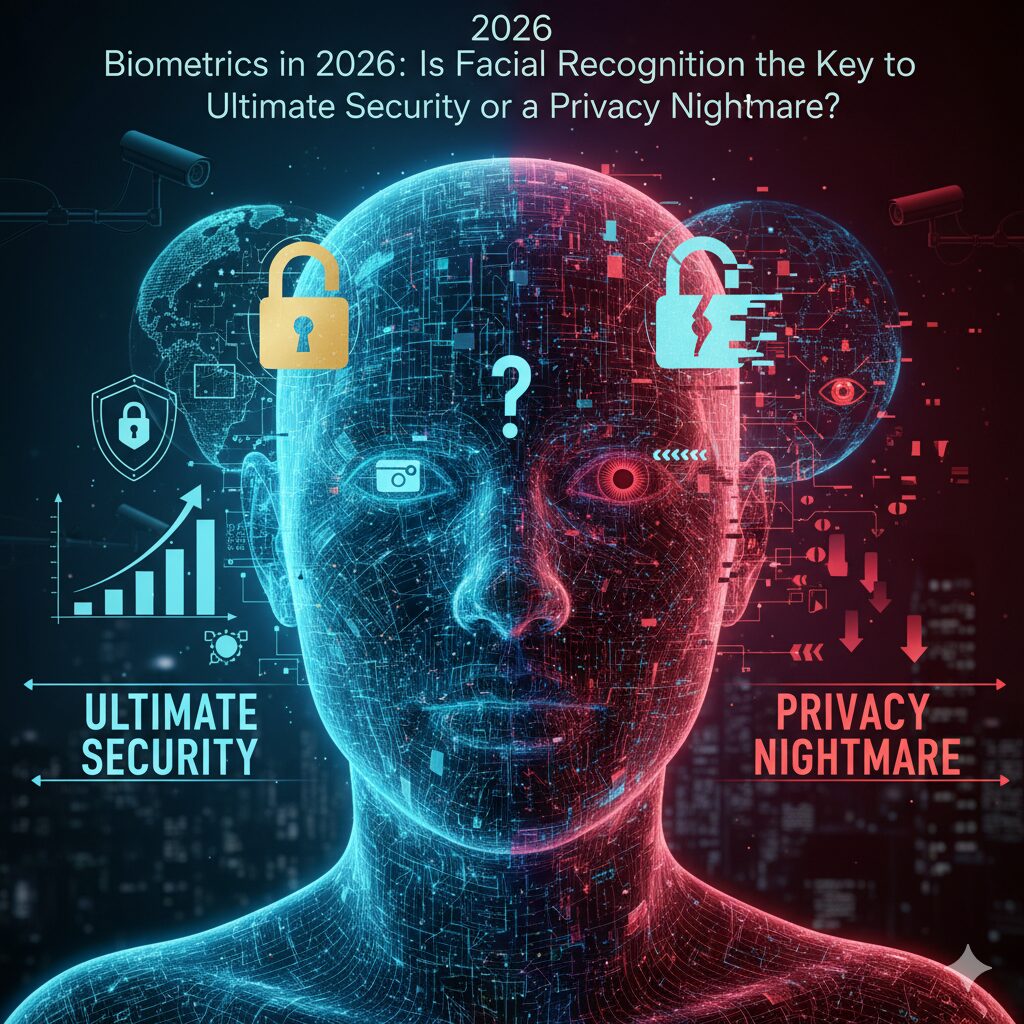
The discussion around security and privacy is reaching a fever pitch, and at its center is the rapid deployment of biometric technologies. Biometrics in 2026 represents a pivotal moment where facial recognition, fingerprint scans, and iris authentication are transitioning from niche security tools to pervasive elements of daily life. While proponents hail facial recognition as the ultimate key to swift, immutable identity verification and heightened security, critics warn that its widespread use heralds an unprecedented era of surveillance and privacy erosion. Understanding the dual nature of Biometrics in 2026 is essential for shaping its ethical future.

Tired of biased reviews? The Secure Patrol rigorously tested the top VPNs for speed, security, and streaming. Get our honest, hands-on verdict on the best VPN services to protect you in 2025. The digital world is a minefield. From your Internet Service Provider (ISP) logging your every move to hackers lurking on public Wi-Fi, you’re exposed. A VPN is no longer a “nice-to-have”—it’s your first line of defense.

A small, toy-like device, often described as a “multi-tool for geeks,” has captured global attention—and sparked serious anxiety among security professionals and homeowners alike. The device is the Flipper Zero, and its capability to interact with nearly every wireless protocol around us has ignited a crucial discussion about digital security.
Is this tiny gadget a harmless penetration testing tool, or does it represent a genuine danger?
The truth is, the capabilities of this device are real, and understanding the core components of The Threat of Flipper Zero is the only way to defend against it. This comprehensive article dives into how the Flipper Zero works, details its ability to compromise smart doors and clone access badges, and provides actionable steps to protect your home and business against The Threat of Flipper Zero.
End of content
End of content