Understanding DNS Amplification Attacks: A Comprehensive Guide
What is a DNS Amplification Attack?
A DNS Amplification Attack is a type of Distributed Denial-of-Service (DDoS) attack. Like all DDoS attacks, its goal is to slow down or completely block user access to systems, services, websites, or applications on a network. Most DDoS attacks are volumetric, meaning they overwhelm the target network with more traffic than it can handle. Imagine thousands of cars suddenly flooding a six-lane highway after a concert or football game, causing a traffic jam. This is a real-world analogy of a DDoS attack.
How Does a DNS Amplification Attack Work?
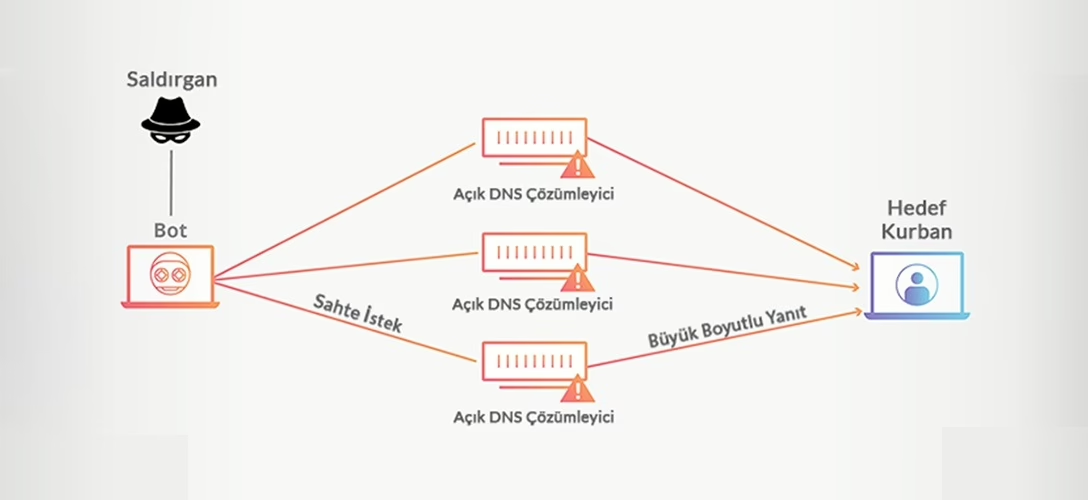
A DNS Amplification Attack involves an attacker using a botnet to send requests to open DNS resolvers. The attacker spoofs the source IP address in the request, replacing it with the target’s IP address. The request is crafted to generate a large response, which is then sent to the target. This type of attack is known as a DNS Amplification Attack, and it can overwhelm the target with a flood of unexpected responses.
The Six Steps of a DNS Amplification Attack
- The attacker sets the source IP address in the DNS request to the target’s IP address.
- The attacker identifies DNS resolvers that will return large responses to requests made using UDP packets with arguments like “ANY”.
- The attacker uses a botnet to send these crafted UDP packets to the DNS resolvers.
- The DNS resolvers respond to the target’s IP address.
- The target receives responses from DNS resolvers it never queried.
- The target’s network infrastructure slows down or becomes overwhelmed due to the high volume of traffic, leading to a denial of service.
Alternative Techniques for DNS Amplification Attacks
Instead of using a large number of average-sized packets, attackers can use a smaller number of larger packets to achieve the same effect. This is like having six large trucks driving side by side on a six-lane highway, slowing down or completely blocking traffic.
How Does a DNS Amplification Attack Work?
In a DNS Amplification Attack, attackers exploit the normal functioning of the Domain Name System (DNS), which is like the internet’s address book. The goal is to flood the target system’s network bandwidth with fake DNS lookup requests until it can no longer provide service.
To understand what a DNS Amplification Attack does, it’s important to first understand DNS. DNS is a protocol that translates domain names (like www.example.com) into their corresponding IP addresses.
The Hierarchy of a DNS Request
When a request is made to a domain address, it follows a specific hierarchy:
- The local DNS cache is checked.
- If the IP address is not found in the local cache, the hosts file on the operating system is checked.
- If the IP address is still not found, the request is forwarded to the DNS servers of the Internet Service Provider (ISP).
- This process continues until the IP address is found.
A company’s own domain network can resolve DNS requests for its employees. However, the internet is full of open DNS servers that respond to DNS requests from anyone, including attackers. Attackers can send malicious requests to these open DNS resolvers by manipulating the source IP address. This can slow down or even crash the target system with a flood of unwanted DNS responses.
The Goal of DNS Amplification Attacks
One of the attacker’s goals is to send small DNS requests that generate large DNS responses. A typical DNS request is usually only a few lines of text, or tens of bytes in size. However, the response to a DNS request can be much larger. This size difference is known as the amplification factor, and it’s what attackers exploit in a DNS Amplification Attack.
Instead of requesting the IP address of a domain like example.com, an attacker might request all the DNS records for that domain. This response could include information about subdomains, backup servers, mail servers, aliases, and more. A sudden 10-byte DNS request could generate a response that’s 10, 20, or even 50 times larger.
The Role of UDP in DNS Amplification Attacks
DNS traffic needs to happen at lightning speed, considering the millions of DNS requests made every day. That’s why DNS resolvers use the User Datagram Protocol (UDP). UDP’s primary function is to transport messages between a server and a client. It doesn’t check if the message was received or if the data was verified, making it a fast but unreliable protocol.
Because UDP doesn’t track the communication between a server and a client, it doesn’t know the source IP address of a request. Attackers can exploit this by manipulating the source IP address in their DNS requests, making it appear as if the request came from the target’s IP address. The DNS resolver then sends the response to the target, overwhelming it with unwanted traffic.
The Advantages of DNS Amplification Attacks for Attackers
One of the main advantages of this type of attack is that the attacker doesn’t need a large number of resources. With just one source IP address, an attacker can significantly reduce the performance of a target site or even take it down completely by sending a massive amount of DNS requests.
For further reading on cybersecurity and DDoS attacks, you can refer to authoritative sources like the US-CERT.