Understanding Deep Link Vulnerabilities in Mobile Apps: A Comprehensive Guide
What Are Deep Links?
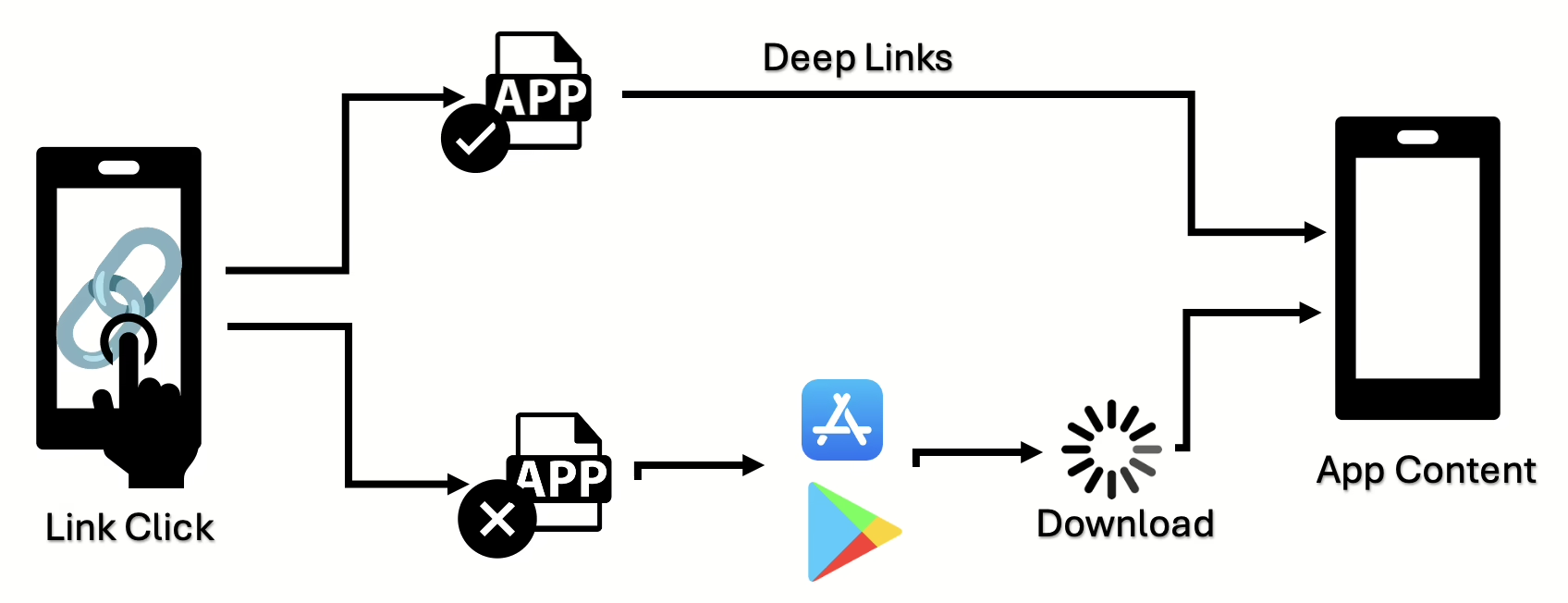
Deep links are specialized URLs designed to directly open specific pages, content, or activities within mobile applications. These links allow users to be automatically redirected to a designated location within an app when they click on a link. For instance, when you see a prompt asking, “Do you want to open this page in the app?” it indicates that a deep link redirection is active. Unlike web page links, deep links aim to direct users straight to specific content or activities within an app.
Types of Deep Links in Mobile Applications
Implicit Deep Links
Implicit deep links contain a specific URL scheme (URI scheme) but do not directly specify which activity to open. The app determines the relevant screen by analyzing the incoming URI data.
Explicit Deep Links
Explicit deep links directly point to a specific activity. The activity to be opened is predetermined and includes a direct class reference (Activity).
Security Vulnerabilities and Impacts of Deep Links
Link Hijacking and Phishing
Link hijacking occurs when a malicious app intercepts deep links intended for another app. This can lead to phishing attacks, where users are tricked into entering sensitive information on fake login screens that appear legitimate.
Data Interception
Deep links can transmit sensitive data such as authentication tokens. If not properly secured, attackers can intercept this data, gaining unauthorized access to user accounts.
Traffic Hijacking
Improperly configured deep links can result in traffic hijacking, where malicious apps register popular URL schemes to redirect users to their own apps instead of the intended ones.
Static Analysis of Deep Link Vulnerabilities
To identify deep link vulnerabilities, a static analysis of the application is necessary. This involves examining the APK file’s contents using tools like Jadx.
AndroidManifest.xml Examination
The AndroidManifest.xml file defines the app’s permissions and components. Intent Filter elements, which specify parameters like scheme, host, and path, are crucial for identifying deep link vulnerabilities.
WebViewActivity and Security Settings
The settings within WebViewActivity can significantly impact the app’s security. For example, enabling JavaScript and universal file access can lead to Cross-Site Scripting (XSS) attacks if not properly configured.