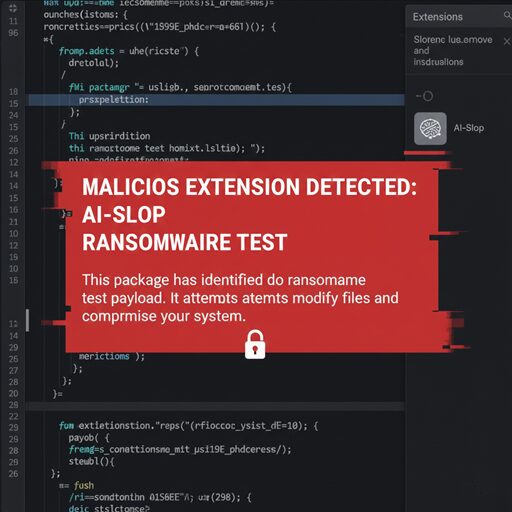
AI-Slop Ransomware Test Sneaks on to VS Code Marketplace – A Developer Security Wake-Up Call
The recent discovery that a malicious package, identified as an AI-Slop ransomware test, managed to bypass security checks and appear briefly on the Visual Studio Code marketplace has sent ripples through the developer community. This incident, while quickly contained, serves as a stark reminder of the persistent supply chain risks inherent in using third-party extensions. The package, reportedly designed to simulate ransomware behavior under the guise of an AI-related utility, was essentially an AI-Slop ransomware test designed for nefarious purposes, highlighting vulnerabilities in the vetting process for popular development tools.
The Nature of the Threat
The so-called “AI-Slop” package was not a fully operational, encrypting ransomware strain, but rather a proof-of-concept or a test designed to demonstrate how easily such a payload could be distributed. By masquerading as an extension related to “AI,” a trending topic, the attacker capitalized on developers’ interest in new tooling.
When executed, the AI-Slop ransomware test likely performed a set of suspicious actions:
This particular AI-Slop ransomware test exposure reveals a critical weak point: the trust developers place in the marketplace ecosystem.
Why Marketplace Security is Paramount
The VS Code Marketplace is a vast repository of extensions that developers rely on daily to enhance productivity. The trust model is simple: if it’s on the official marketplace, it must be safe. The success of the AI-Slop ransomware test in breaching this trust highlights several key security concerns:
Immediate Action and Future Implications
While Microsoft acted quickly to remove the package, the incident underscores the need for continuous security hardening. Users who may have downloaded the AI-Slop ransomware test extension should immediately review system logs, isolate affected machines, and check for any unauthorized file modifications or outbound network connections.
For the future, the industry must focus on developing better mechanisms to verify the integrity and origin of all extensions. The lesson from the AI-Slop ransomware test is clear: the convenience of easy installation must be balanced with rigorous, multi-layered security protocols to protect the global development community from increasingly clever social engineering and hidden malware payloads.
A malicious extension with basic ransomware capabilities seemingly created with the help of AI, has been published on Microsofts official VS Code marketplace.
Named susvsex and published by ‘suspublisher18, the extensions malicious ality is openly advertised in its description.
Secure Annex researcher John Tuckner discovered susvsex and says that it is the product of “vibe coding” and is far from sophisticated.
Despite its seemingly simple nature, the susvsex extension poses a significant threat to developers who may unknowingly install it. The extension’s primary function appears to be encrypting files in a designated directory, rendering them inaccessible without a decryption key. This type of ransomware attack is particularly concerning as it can lead to potential data loss and disruption of ongoing projects for developers.
Ransomware attacks have been on the rise in recent years, with cybercriminals increasingly targeting developers and organizations that rely on open-source software. The susvsex extension serves as a stark reminder of the vulnerabilities that can exist within popular development platforms. As developers integrate various plugins and extensions into their workflows, the risk of inadvertently installing malicious software increases.
To protect against such threats, developers are advised to exercise caution when installing extensions from marketplaces. It is essential to review the extension’s description, ratings, and user reviews before proceeding with installation. Additionally, maintaining secure backups of important projects can serve as a safeguard against potential data loss caused by ransomware.
Moreover, it is crucial for developers to ensure that their development environments are equipped with up-to-date security measures. This includes using antivirus software, enabling firewalls, and regularly updating both the code editor and its extensions. By taking proactive steps, developers can mitigate the risk of falling victim to ransomware attacks like the one presented by susvsex.
The emergence of AI-generated malicious software raises further concerns about the future of cybersecurity. As artificial intelligence technology continues to advance, the potential for cybercriminals to create more sophisticated and evasive ransomware strains increases. This evolution necessitates a shift in how developers and security professionals approach threat detection and response.
In response to the growing threat of ransomware, organizations are now prioritizing cybersecurity training for developers and staff. By fostering a security-first mindset, teams can better recognize potential threats and respond effectively. Regular training sessions that cover best practices for software development, safe browsing habits, and incident response protocols are essential in building a resilient workforce.
Furthermore, collaboration within the developer community can serve as a powerful tool against ransomware. Sharing information about newly discovered threats and vulnerabilities can help raise awareness and prompt quicker responses. Initiatives that encourage developers to report suspicious extensions or plugins can create a safer environment for all users.
As the cybersecurity landscape continues to evolve, it is vital for developers to stay informed about the latest threats and protective measures. Keeping abreast of industry news, participating in forums, and engaging with cybersecurity experts can provide valuable insights into emerging risks.
In conclusion, the discovery of the susvsex ransomware extension on the VS Code marketplace highlights the ongoing battle against malicious software in the development community. Developers must remain vigilant and proactive in their approach to cybersecurity to safeguard their projects and sensitive data. By adopting best practices and fostering a culture of security awareness, the risk of ransomware infections can be significantly reduced, ensuring a safer development environment for everyone.






