7-Layer Model for Protecting Your Digital Fortress
In the dynamic cyber landscape of today, effective security requires a comprehensive, multi-layered strategy. Simply relying on a single firewall or antivirus solution is insufficient for Protecting Your Digital Fortress. Instead, security leaders must adopt an architectural approach—a model that views the organization’s assets as a Digital Fortress requiring defense at every conceivable entry point. This 7-Layer Model for Protecting Your Digital Fortress provides a structured framework for CISOs and security professionals to audit, build, and optimize their defense posture, ensuring robust security from the perimeter to the core.
Why a Layered Approach is Crucial for Protecting Your Digital Fortress
The principle of “Defense in Depth” dictates that failure in one security control should not lead to complete compromise. By implementing seven distinct layers, you create redundancy, ensuring that an attacker who bypasses Layer 1 still faces six additional obstacles before compromising critical assets. This integrated strategy is the key to successfully Protecting Your Digital Fortress.
The 7 Layers for Protecting Your Digital Fortress
Layer 1 – The Perimeter (Network Security)
This is the outermost wall of your Digital Fortress. It manages traffic entering and leaving your network.
Layer 2 – Access & Identity (Authentication)
This layer verifies the legitimacy of users and systems attempting to access resources—a fundamental aspect of Protecting Your Digital Fortress.
Layer 3 – Endpoint Protection (Device Security)
This layer focuses on the devices used by employees (laptops, mobile phones, servers), which are frequent targets for initial compromise.
Layer 4 – Application Security
With increasing use of proprietary and third-party software, this layer protects the code and functionality of applications themselves.
Layer 5 – Data Security (The Crown Jewels)
This is perhaps the most critical layer for Protecting Your Digital Fortress as it focuses directly on the assets you are trying to defend: the data itself.
Layer 6 – Visibility & Intelligence (Monitoring and Detection)
This layer acts as the eyes and ears inside the Digital Fortress, constantly looking for signs of intrusion or compromise.
Layer 7: Human Factor (Awareness and Training)
Often cited as the weakest link, the human layer is vital for Protecting Your Digital Fortress.
Architectural Success in Protecting Your Digital Fortress
The power of this 7-Layer Model for Protecting Your Digital Fortress lies in its synergy. Alerts from the Data Layer (L5) might be cross-referenced with logs from the Visibility Layer (L6), confirming a perimeter breach that was initially missed by the Network Layer (L1). By implementing robust controls across all seven layers, organizations achieve true Defense in Depth, making the cost and effort of attack prohibitively high for cybercriminals. In today’s hyper-connected world, data isn’t just important; it’s the new currency. It’s the lifeblood of your business, the core of your operations, and the foundation of your customer relationships. And where does this digital gold reside? In a data center. But with this immense value comes immense risk. Data centers are high-priority targets for everyone from sophisticated cybercriminals to physical intruders. A single breach can be catastrophic, leading to devastating financial losses, regulatory fines, and irreparable damage to your reputation.
So, how do you protect this digital fortress? A single padlock or one strong firewall won’t cut it. The solution is a comprehensive, layered security approach. Think of it like a medieval castle: you don’t just have one high wall. You have a moat, an outer wall, an inner wall, towers, and guards, all working together. This “defense-in-depth” strategy is the core of the 7-layer data center security model. Let’s break down each layer, from the outside in.
Layer 1 – The Perimeter (Site Property)
This is your first line of defense. It’s all about securing the physical land your facility sits on, long before anyone can touch the building.
Layer 2 – The Facility (Building Shell)
Once past the perimeter, an intruder faces the building itself. This layer focuses on making the structure a “hard target.”
Layer 3 – The “White Space” (Data Hall)
This is the secure room where the servers and equipment actually live—the “crown jewels” of the physical facility.
Layer 4 – The Rack & Cabinet
We’re now inside the data hall, but the security doesn’t stop. The individual server racks provide the fourth layer.
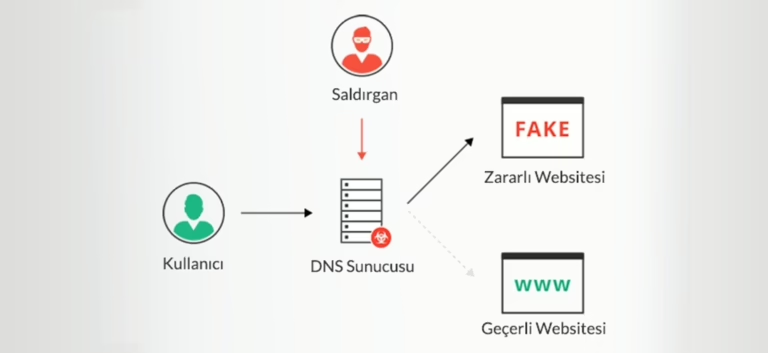
Layer 5 – The Network (The Digital Perimeter)
Layers 1-4 were physical. Now, we move to the logical (digital) security that protects the data in transit.
Layer 6 – The Host (The Server Itself)
If a threat were to bypass the network, it would next try to attack the server or operating system.
Layer 7 – The Data (The Crown Jewels)
This is the final and most crucial layer. If all else fails, how do you protect the data itself?
Your Fortress is Only as Strong as Its Weakest Layer
Protecting a data center isn’t about choosing between physical security and cybersecurity. It’s about creating a single, unified strategy where every layer supports the others. The best data center security practices recognize that a digital firewall (Layer 5) is useless if someone can walk in and steal the server (breaching Layers 1-4). Likewise, the strongest fence in the world (Layer 1) won’t stop a hacker who can exploit an unpatched server (Layer 6).
By implementing a robust 7-layer model, you build a true digital fortress that protects your organization’s most valuable asset from every conceivable angle.