The Importance of Dorks in Passive Information Discovery
The Dorks open source intelligence these are queries that are used to collect and identify potential security vulnerabilities and are carried out for the purpose of obtaining clear results. Within the scope of cyber security dork usage(asset) will help you easily identify methods and exploits to be used to discover weak points and overcome defense mechanisms for the targeted digital asset (asset). the word “Dork” is the general name given to queries containing certain parameters in search engines. These parameters are used to filter search results and identify targets that meet certain criteria. Dorks can be used for a variety of purposes, but in the field of cybersecurity they are often used to discover vulnerabilities and gathering open source intelligence it is used for.
Open Source Intelligence (OSINT)
Dorks can be used to discover sensitive information or vulnerabilities in open source projects, forums, blogs, and other online resources. For example, dorks can be used to find documents of a particular company or files containing customer information.
Vulnerability Analysis
Dorks can be used to find vulnerabilities in a specific software or platform. For example, you can detect affected sites by using dorks for an opening commonly used in a web application.
User ID Discovery
Dorks can be used to detect files containing passwords/passwords or authentication information that may be used in future attacks. For example, you can search for passwords or usernames on files with a specific file extension.
The queries to be created are basically no different from querying a database. It is necessary to design the query to be prepared for the main data to be accessed in a way that narrows it from general to specific.
For example “com.eslet’s say we went hunting for content published on the ” (Spain) domain and we want to view all pages with the “.es” extension. If we expressed this with a SQL query it would look like this.
SELECT page_URL FROM google.all_pages
WHERE page_url LIKE '%com.es%';But we can easily achieve this on Google with simply one operator:
inurl:"com.es"
or
site:com.esDepending on the intended use, you can also obtain other operators by searching for the platforms on which they will be used. For example; “google dorks cheat sheetyou can access comprehensive operator lists with a search like ”.
Let’s take a look at how dorks are used on the following three platforms, which are widely preferred globally for open source intelligence and vulnerability discovery. Here we select three platforms for review:
Of course, there are also many vehicles.
Google Search Engine
Google Dorkingas a hacker technique, it aims to find vulnerabilities in the configuration and code of websites using Google Search and other Google applications. Google Dorking, also OSCINT it can be used to combine these vulnerabilities to explore broader vulnerabilities and gather more information.
Let’s assign a customized query for a targeted industry. Let’s say we chose the education sector. Terms that may be included in the activity, personal information, financial planning, etc. You can customize your queries with keywords related to. Let’s see how we can access critical information with some sample commands below…
Dork query example where sensitive information can be obtained about institutions operating in the education sector:
inurl:edu.tr results | income | password | db | tckn | “password” | classified | "service specific" | "secret" filetype: pdfLet’s say we used the following dork by saying that we are looking for a direct site or different critical information hosted on WordPress-based sites, and let’s simply see what we were able to achieve:
inurl:"wp-content/uploads" intext:credential | passwordThese queries can also be provided automatically. For example; Dorks Eye the named tool uses Google dorks automatically to detect security vulnerabilities on target websites. The tool can help you quickly find pages containing sensitive information such as usernames, passwords, passwords, database names. You can easily access the vehicle related to your search on the Github repo, along with the instructions for use. However, you should not forget your ethical and legal responsibilities when using such tools.

Shodan Search Engine
Shodan Search Engine it is used by security researchers in network scans and vulnerability detection processes. Shodan search engine it can be used to detect various internet-connected devices such as IP cameras, routers, servers, SCADA systems. With Shodan’s unique dorks, potential vulnerabilities in these devices can be revealed by targeting specific products, brands or protocols using specific search terms or filters. With the outputs obtained using these dorks, certain network devices (for example; cameras, routers, servers), services and ports can be targeted.
The main difference between them and Google SE can be distinguished as Shodan scanning the internet and the other scanning www. Shodan“collects information by interacting with web services and stores this information in an object called ” Banner. Thus, one Dorkwhen you search for anything using ‘, Shodan receives information from the relevant service temporally from its banner, obtained in short loops, and presents it to you. In simple terms, “Banner” is a structure that contains metadata about a service.
Shodan’s banner information is based on data published by various devices and services and found in network traffic. For example, a server’s banner information may include the server’s operating system, software versions used, open ports, and other related information. Banner information of different devices such as cameras, routers, databases may reflect the specific features and configurations of these devices.
Let’s see how we can perform the relevant operations on the Shodan side…
Let’s find a mission first.. “ in Turkey edu.tr” can be successfully accessed on web servers serving on the “ domain Index of /Let’s list the ” pages. Our command will be:
http.html:"Index of /" country:"TR" hostname:"edu.tr"You will get a long result output. Let’s choose one of them.
As seen in the banner information, you will have a lot of details about the server and the services used in it. Additionally, there are vulnerabilities listed in the detail page that match the information contained in the banner.
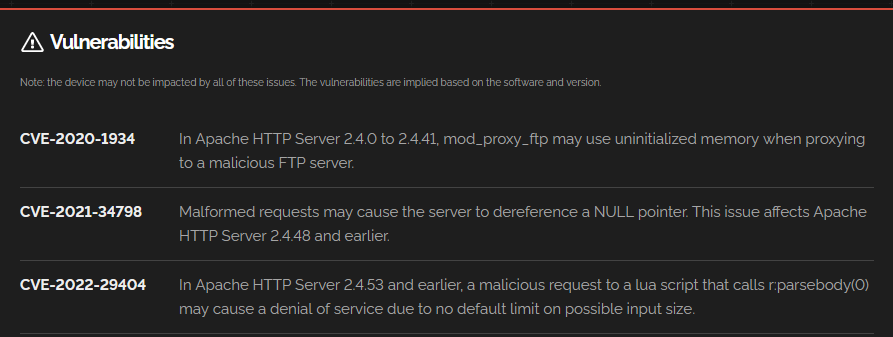
when we visit the “Index of /” page, we come across files belonging to the application under the directories. Let’s assume that it is the application used for a critical service. Reverse engineering etc. Various exploits can be achieved with analyzes that can be made with techniques.
Again, as we mentioned in the Google Dorking section, “Shodan darks” you can easily access operator lists that you can use for your ” type searches and advanced queries.
GitHub Repos
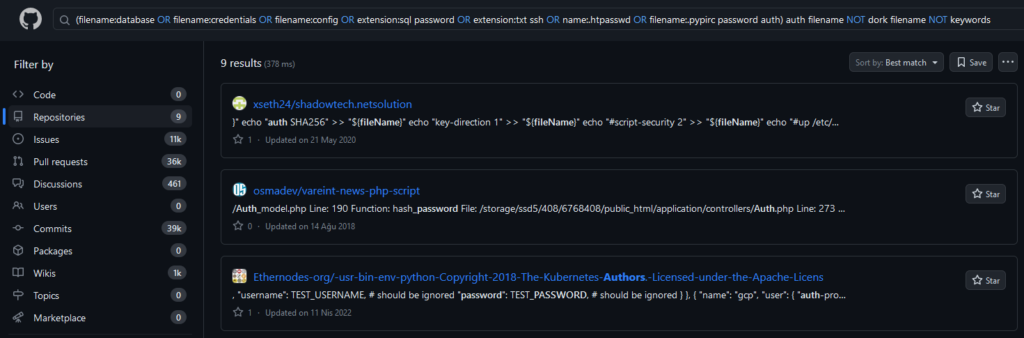
Github, also widely known, is a popular platform where developers can store code, collaborate and manage projects. It is home to millions of public code repositories. These repositories may contain important information such as software, configuration files, passwords, and sensitive data written by developers. This is where dorks may come into play again. In open source projects, you may have the opportunity to detect potential security vulnerabilities and warn developers.
In addition to the parameters you can use in the search section, you can diversify your queries with different operators (AND, OR, NOT, etc.) as well as operating operands. The biggest handicap you can experience in achieving the right result here is that some repo owners attach lists related to dorks in repetitive and bulk form to one part of their repos in order to be visible. Repeated dork query results included in the lists will prevent you from accessing useful information.
To prevent this, it will be sufficient to develop the parameters that will provide exclusion for unnecessary query outputs yourself and include them in your queries.
filename NOT dork filename NOT keywordsThe query below, for example, will give you access to content that may contain critical levels of information in various materials in repos:
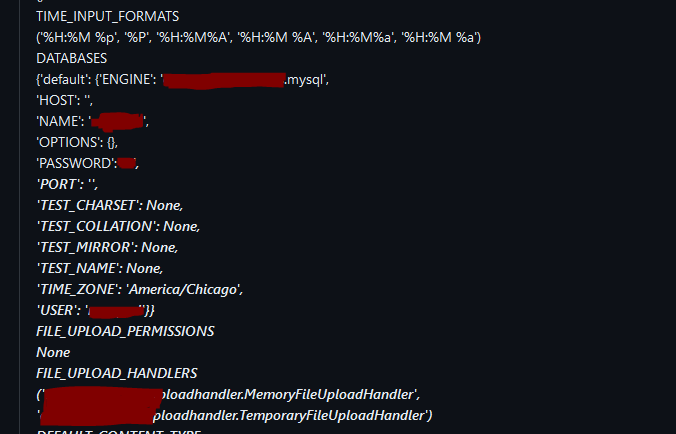
From a query return obtained, it enabled us to display critical information about the database integrated into the relevant systems, such as user, password, database name, in cleartext format.
As examples show, the use of dork is a valuable tool for cybersecurity researchers and ethical hackers. Apart from the three headings mentioned here, information discovery can be diversified through query methods on different platforms that contain widely used service/service information. It would not be surprising if important information beyond predictions is revealed in a targeted, deeper information gathering adventure enriched with information obtained from different points. Especially today, due to reasons such as the widespread use of open source intelligence opportunities, the preference of new platforms in business development processes, and the incorrect configuration of digital assets where information is located, this method will lead to the acquisition of critical/confidential information for activities with an unpredictable ease.
However, as we mentioned before, it is important to use dorks within ethical and legal limits. Accessing sensitive data or attacking networks without permission is illegal and unacceptable.