NordVPN vs ExpressVPN – Which One is Actually Better in 2025?
It’s the ultimate VPN showdown. We put NordVPN vs ExpressVPN head-to-head in a rigorous, hands-on test…
Cyber Security
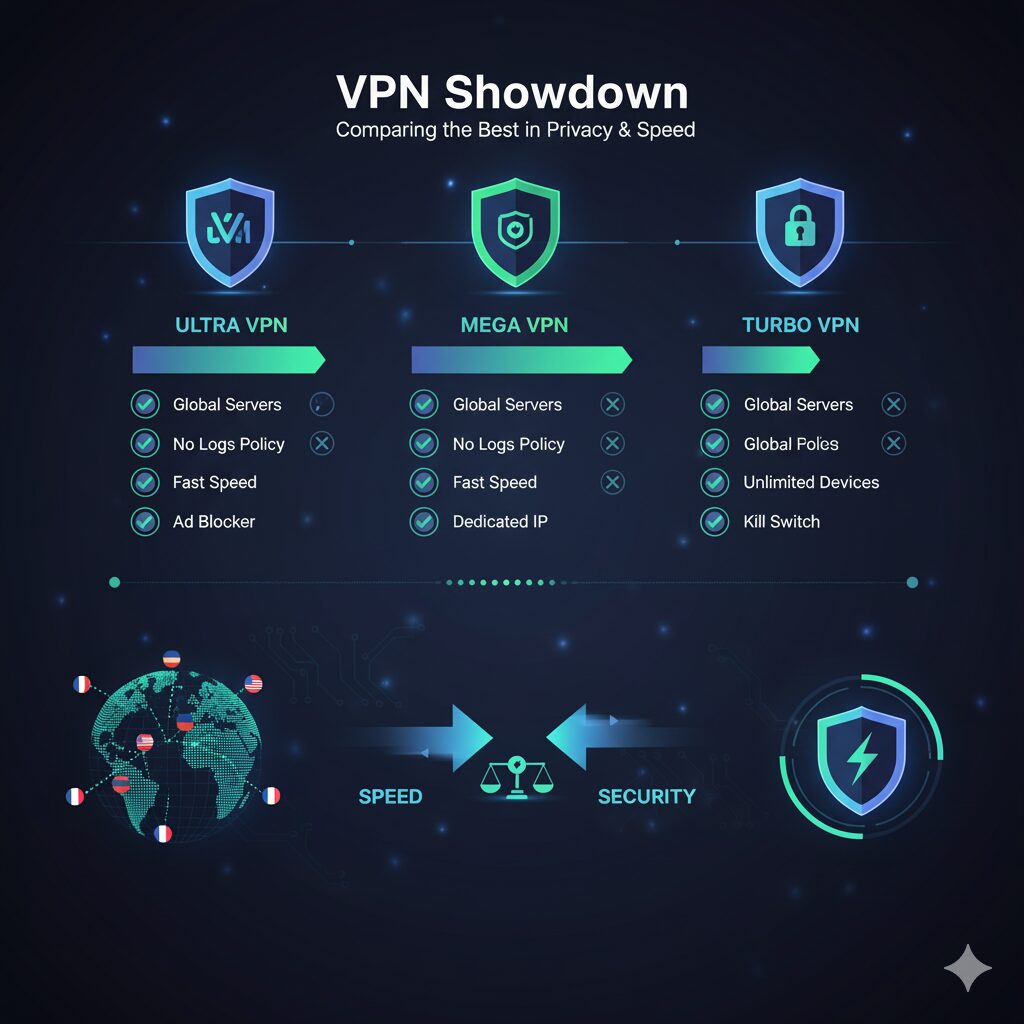
It’s the ultimate VPN showdown. We put NordVPN vs ExpressVPN head-to-head in a rigorous, hands-on test…

Artificial intelligence in cybersecurity is revolutionizing threat detection and response with machine learning algorithms that analyze millions of security events per second and identify patterns that humans cannot perceive. According to IBM’s Artificial Intelligence Security Report, businesses using artificial intelligence in cyber security reduce incident response times by 70% and reach a threat detection rate of 98%. This technology processes large data sets to predict cyber attacks, automate defenses, and adapt to evolving threats faster than traditional security methods. businesses implementing AI-driven security save 150 billion dollars annually thanks to improved threat prevention and reduced breach costs. Security teams leverage artificial intelligence to combat deepfakes, automated phishing, and advanced cyberattacks targeting critical infrastructure.

The recent discovery that a malicious package, identified as an AI-Slop ransomware test, managed to bypass security checks and appear briefly on the Visual Studio Code (VS Code) marketplace has sent ripples through the developer community. This incident, while quickly contained, serves as a stark reminder of the persistent supply chain risks inherent in using third-party extensions. The package, reportedly designed to simulate ransomware behavior under the guise of an AI-related utility, was essentially an AI-Slop ransomware test designed for nefarious purposes, highlighting vulnerabilities in the vetting process for popular development tools.

Aura vs LifeLock: Which identity theft protection is truly better? We compare features, 3-bureau credit monitoring, VPN, antivirus, family plans, and pricing for 2025. Find out who actually protects you.

Cyber attacks; It is all intentional and malicious actions taken by an individual, group or government…

For decades, the password has been the undisputed gatekeeper of our digital lives. Yet, year after year, headlines scream about massive data breaches, and users groan under the weight of “password fatigue.” Even the venerable Master Password, the core of your password manager, is an increasingly vulnerable single point of failure.
In 2025, the conversation is no longer about managing complexity; it’s about embracing simplicity and true security. The era of the alphanumeric string is over. The definitive answer to digital authentication is here, and it is time to shift your perspective on Passkeys vs Passwords.
This comprehensive guide breaks down the critical differences in the Passkeys vs Passwords debate, illuminates the superior security model of passkeys, and provides a compelling argument for why this is the year you finally move past the master password paradigm.

Data Breach Prevention Strategies: A Comprehensive Guide for Beginners In today’s interconnected world, data breaches are a constant threat to…

What is a VPN? It’s your personal digital privacy shield. We break down how a VPN stops hackers, blocks ISP tracking, and unlocks a more open internet for you in 2026. Let’s cut to the chase. The internet is a digital gold rush, and your personal data is the gold. Ever get that creepy feeling when an ad for something you just talked about shows up on your phone? Or maybe you’ve used the free Wi-Fi at an airport, feeling a little exposed?

The guide to protecting your online identity is mandatory. In today’s hyper-connected world, your online identity is often more valuable—and vulnerable—than your physical belongings. It is the summation of your data, passwords, interactions, and reputation across every digital platform. Therefore, mastering the Guide to Protecting Your Online Identity is mandatory, not optional, for every internet user. Neglecting this crucial aspect leaves you exposed to everything from financial fraud to identity theft. This comprehensive Guide to Protecting Your Online Identity will walk you through the essential steps to secure your digital presence and ensure you are truly safe in the digital age.

The Dorks open source intelligence these are queries that are used to collect and identify potential security vulnerabilities…
End of content
End of content