The 5 Best Crypto Hardware Wallets – Our Top Picks for Securing Your Assets
With the crypto market booming, is your portfolio actually safe? The reality is, cold storage is your only true…
Cyber Security

With the crypto market booming, is your portfolio actually safe? The reality is, cold storage is your only true…

A small, toy-like device, often described as a “multi-tool for geeks,” has captured global attention—and sparked serious anxiety among…

Nucleia ProjectDiscovery it is a fast and open source security vulnerability scanning software developed by his team, written in Go language,…

Get Ready to Transform Your Kodi Streaming Experience Prepare to take your Kodi streaming adventure to the next level!…

Twitter Bitcoin Scam – Wave of cyber attacks, hackers targeted and compromised the verified Twitter accounts of several prominent…

Tired of biased reviews? The Secure Patrol rigorously tested the top VPNs for speed, security, and streaming. Get our…

Learning how to Spot a Phishing Email is one of the most critical cybersecurity skills you can acquire in…
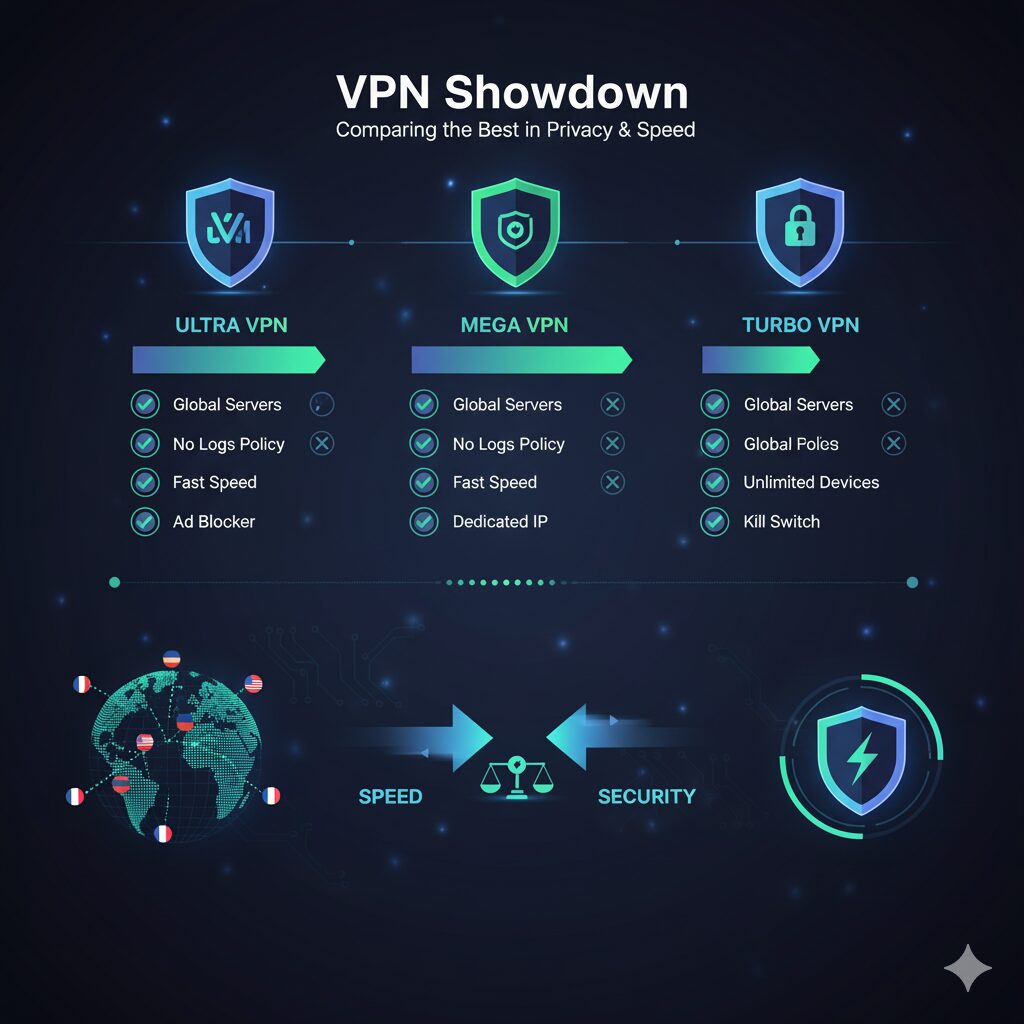
It’s the ultimate VPN showdown. We put NordVPN vs ExpressVPN head-to-head in a rigorous, hands-on test of speed, security,…

What is a VPN? It’s your personal digital privacy shield. We break down how a VPN stops hackers, blocks…

Stop reusing passwords! We put LastPass vs 1Password head-to-head for security, features, and ease of use. The Secure Patrol’s…
End of content
End of content